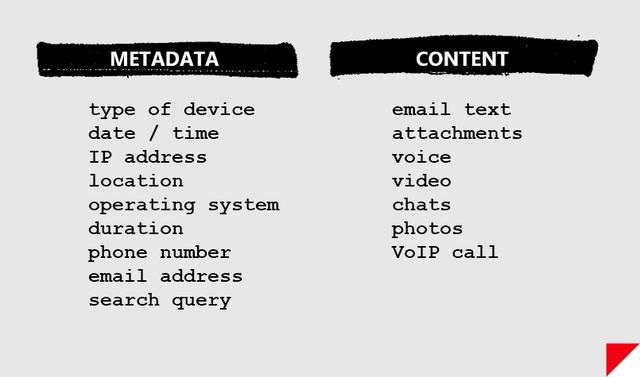
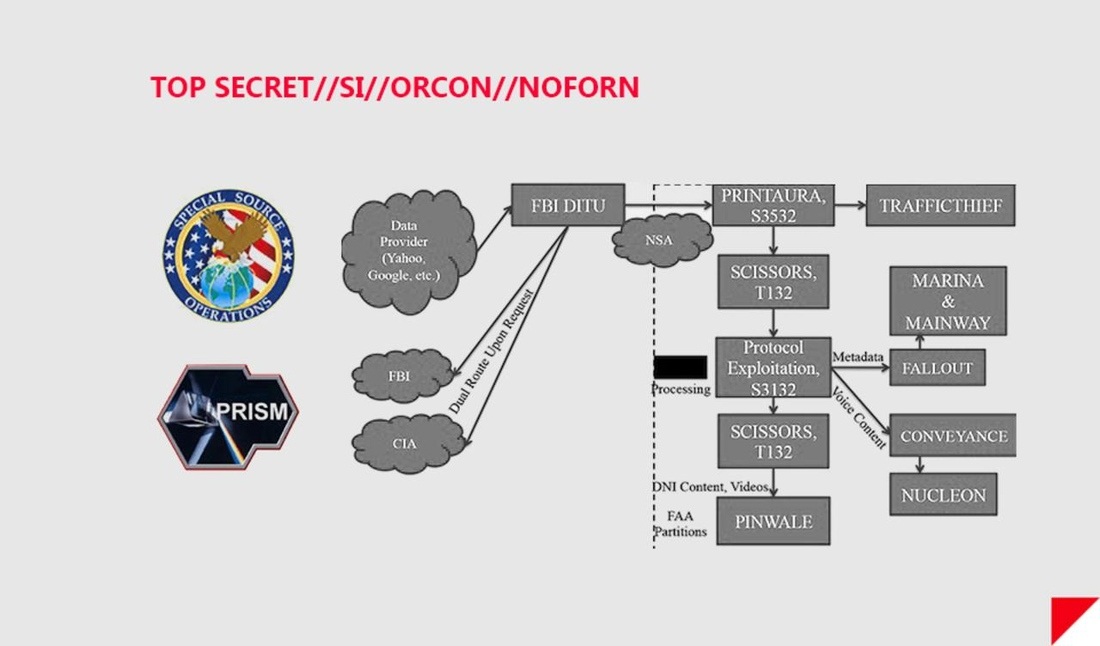
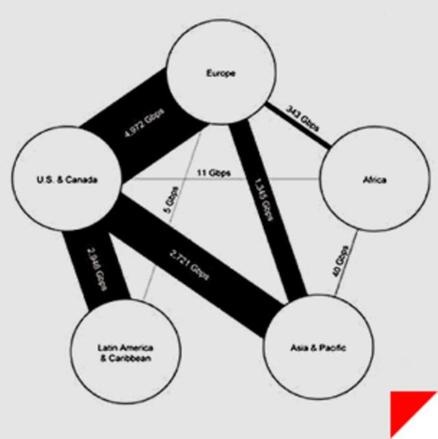
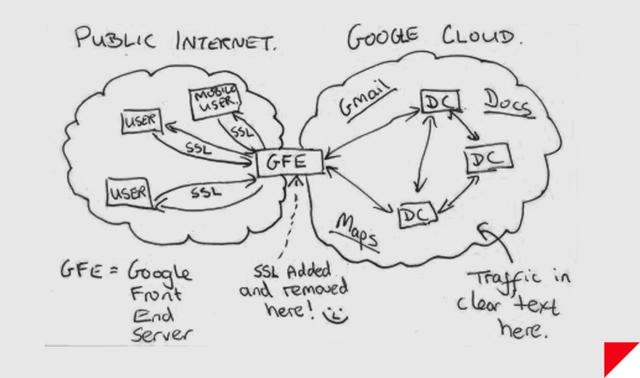
"I know the capability that is there to make tyranny total in America, and we must see to it that this agency and all agencies that possess this technology operate within the law and under proper supervision, so that we never cross over that abyss. That is the abyss from which there is no return." Senator Frank Church on Meet The Press, 1975 On November 4th, 1952, a new federal agency was created in secret, chartered with spying on foreign adversaries around the world. There was no mention in the press. There was no discussion on the floor of Congress. The existence of the agency appeared nowhere in the Federal Register. Since then, much of what the public knows about the National Security Agency has been the stuff of Sneakers and West Wing legend. Its budget — part of the secretive US “black budget” — is largely unknown. The NSA has even been nicknamed “No Such Agency” because of its extreme secrecy. Its headquarters, located in Fort Meade, Maryland, literally resembles a giant black box. But this year, the box was cracked open. An unprecedented cache of the NSA’s secrets were stolen in bulk this year by a single independent contractor with administrative access to the intelligence community’s network — a feat unmatched by previous NSA whistleblowers who provided the world mostly with eyewitness accounts of the agency’s behavior. The former contractor, Edward Snowden, fled the United States before teaming up with journalists to disseminate the NSA files, and now resides in Russia where he sought asylum and protection from US prosecution. We now know that nearly five decades after its creation, the NSA began to operate what would become a global surveillance network of breathtaking scale. Today, it collects records about every phone call placed in the United States. It works with overseas partners and telecommunications companies to directly tap into the arteries of the internet, and scoops up massive amounts of data including emails, chats, VoIP calls, and more. It collects billions of records every year, many belonging to ordinary US citizens with no suspicion of wrongdoing. Nearly each week since June 5th when The Guardian published the first Snowden documents, new internal files and facts about bulk NSA surveillance have been released. Snowden is said to have leaked upward of 50,000 files from the government. The journalists to whom he's passing the data, like Glenn Greenwald, say more revelations are coming. SIGNALSSignals intelligence, or SIGINT, encompasses the interception of electronic signals and communications intelligence, and was an enormous factor in 20th-century wars and diplomacy. In World War I, when radio was still a novel concept, the US and other nations primarily gained access to communications by tapping undersea telephone cables. The United States entered World War I after British intelligence intercepted a coded telegram in which the German Empire proposed that Mexico join Europe’s Central Powers, if the US joined the fight on the side of Britain and France. The role of SIGINT was dramatically expanded in World War II, which was a truly global war with widespread use of radio and encoded communications. Cryptography and cryptanalysis were essential to all sides, and intensive code-breaking efforts aided Allied forces greatly in their victory. In 1952, President Harry Truman issued a memo which led to the creation of the National Security Agency, consolidating the military’s SIGINT responsibilities. In the decades following, the NSA would play a crucial role in signals intelligence during the Cold War, the Vietnam War, and in the modern war on terrorism. Even before the pivotal national security era that began on September 11th, 2001, the NSA recognized the SIGINT opportunities presented by the internet. In an unclassified December, 2000 transition report, the agency outlined the intelligence landscape, noting “the explosion in global communications,” and a need to be at the forefront of advances in technology. The document states that “to perform both its offensive and defensive missions, NSA must ‘live on the network.’” As leaked documents from Edward Snowden show, the NSA has largely accomplished the mission it envisioned more than a decade ago. But according to critics, it has systematically dodged or violated federal law in doing so. Following 9/11, the NSA’s ability to gather the communications of US citizens was greatly enhanced by the Patriot Act of 2001, the Protect America Act of 2007, the FISA Amendments Act of 2008, and secret interpretations of US law that have only recently begun to enter the public view — interpretations that have surprised and concerned even the Patriot Act’s original authors. Documents leaked this year have revealed that the NSA is operating a massive global surveillance network, one that once seemed only possible in Hollywood fantasy, and that privacy advocates and some politicians fear is highly intrusive, dangerous, and unwarranted. Furthermore, the surveillance of US citizens appears to go well beyond the NSA’s explicit charge of collecting data “for foreign intelligence and counterintelligence purposes” as set forth in Executive Order 12333. Instead of just collecting data on foreigners, the NSA now appears to want all available communications data in the pursuit of terrorists. INTELLIGENCEIf you have a phone and a computer, it’s likely that practically everything you do generates a signal: your bank records, your emails, your phone calls, your text messages, and your sexy Snapchats. At some point, they’re likely to be handled by companies like Google, Facebook, Apple, or AT&T. And like the NSA, your records live on the network. Unlike documents in a safe or money in a bank vault, your electronic files probably aren’t sitting in one place, especially if they’re handled by global service providers like Google or Yahoo. In the age of global cloud data, it’s possible (even likely) that information you store with a US company is exchanged between servers located outside of US borders. Because of legal restrictions regarding how the NSA is able to collect and search data, there’s an important distinction between the types of intelligence that the agency scoops up. There’s “content,” which is, naturally, the substantive matter of your communications. That includes the stuff inside your emails, the things you say in your phone calls, and the family photo album you store in Dropbox. Then there’s “metadata,” which is “data about data:” it’s information about your content. For phone records that includes data like the times, addresses, and durations of phone calls. For email addresses that includes stuff like the IP addresses and the email addresses of the sender and recipient, and the date and time of the email. A metadata map can tell someone much |









 RSS Feed
RSS Feed