|
by Paul Ducklin on November 1, 2013 | 15 Comments FILED UNDER: Featured, Malware A number of readers have asked us, "What do you guys have to say about the BadBIOS story that's unfolding at the moment?" In a nutshell, it's a story about a virus that is claimed to have some remarkable characteristics. Sufficiently remarkable, in fact, to inspire Ars Technica's Dan Goodin to describe it as not just "mysterious" but "omnipotent." What it doesHere are some of the claims that have been made about the BadBIOS virus:
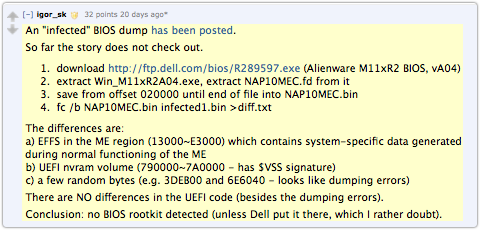
By now, you may be thinking that this sounds more like a science fiction movie than real life. In fact, if you're a certain age, you may well be waiting for Jeff Goldblum to burst forth with a Mac, some mysterious and onmipotent file transfer software, and a countervirus that will save the planet. You're probably also thinking that with as many symptoms, twists, turns and apparent tell-tales as are listed above, we ought to know a lot about it after three years. The thing is, all the facts above come from one observer on Twitter, @dragosr, the guy who runs the CanSecWest, Eusec and PacSec security conferences. The abovementioned details have only come out in the past short while, so we can collectively be excused for not knowing an awful lot just yet. What we knowOne BIOS sample file has been made available; SophosLabs took a brief look and largely concurred with an already-public analysis published on Reddit. (For the record, our analysts didn't see the Reddit story until after they'd looked at the file.) The BIOS we saw seems all but identical to an official Dell Alienware BIOS, so it would be no use on a Mac, for example. And even if a byte-by-byte analysis of the whole BIOS were to reveal a pre-planted backdoor, that would nevertheless only be one small part of the whole story. Furthermore, the software defined radio and speaker-to-microphone infection vectors mentioned above, as a vehicle for jumping airgaps, sound highly speculative. Not impossible, of course - never say impossible where malware is concerned, not least since Stuxnet appeared - but certainly very unlikely. Spreading via USB sticks, like Stuxnet did, would surely be a satisfactory explanation on its own (though the part assuming automatic code execution via USB on multiple operating systems sounds highly speculative, too). Imagine that you could reliably get an infected system to beam out radio waves in the absence of any radio hardware, for example by relying on some serendipitously-located internal circuit parts to serve as your transmitter and antenna. Imagine that you could somehow turn on the speaker and produce reliably-decodable but inaudible sounds. How would you persuade the uninfected computer to receive them at all, let alone to treat them as shellcode that would ultimately let you reflash the BIOS? What we can predictSo the short answer to the question of what we have to say about BadBIOS is, "We can't yet say." Based on @dragosr's tweets, it looks as though additional information, including access to affected USB sticks, will become available at the PacSec conference in Tokyo in just under two weeks' time; until then, says Dragos, he's got to knuckle down to prepare for the event. And, talking of the event, there are various papers about firmware and BIOS level attacks at PacSec 2013, so let's hope that one or more of them will shed some light on what's true and false about BadBIOS. Until then, it's a bit like the dilemma we faced nearly five years ago when the Conficker virus came out and stood poised to do something new on 01 April 2009. Everyone wanted to know what it would do, but all anyone could say with honesty was, "We shan't know until 01 April." What to do about BadBIOSI don't think there is any need for alarm over the BadBIOS story. There isn't an obvious threat to everyone (like there was with Stuxnet, even before we knew its inner purpose); it doesn't seem to be spreading in the wild (like Stuxnet was, despite having a specific target); and there are plenty of clear and present threats we can usefully concern ourselves with in the interim. So that's about that for now, I'm afraid - it's a question of watching and waiting. NB. It's possible, of course, that this is an elaborate hoax, intended as a combined publicity exercise and social engineering experiment that will be wrapped up at PacSec. If so, expect it to be aimed at outing anyone who jumped to detailed conclusions without having the details to go on! http://nakedsecurity.sophos.com/2013/11/01/the-badbios-virus-that-jumps-airgaps-and-takes-over-your-firmware-whats-the-story/
Comments are closed.
|
Archives
March 2021
|
 RSS Feed
RSS Feed