|
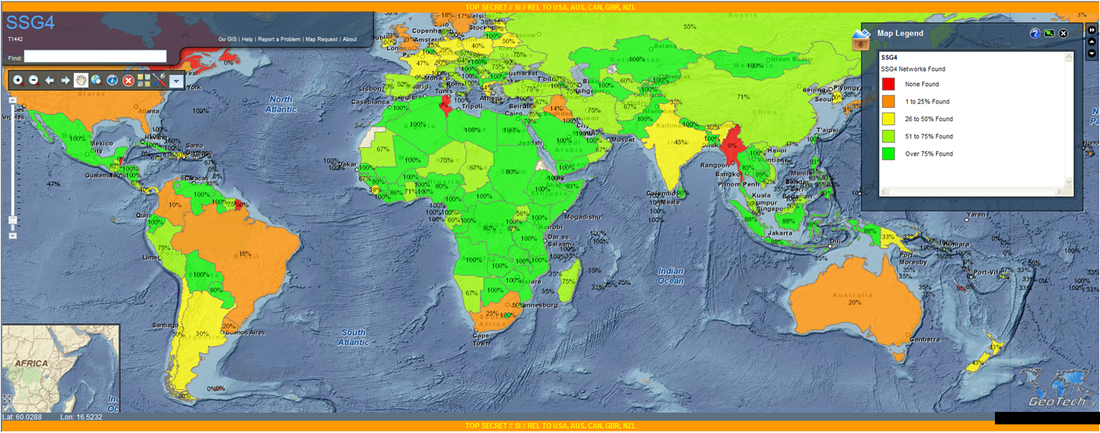
The National Security Agency has spied on hundreds of companies and groups around the world, including in countries allied with the US government, as part of an effort designed to allow agents to hack into any cellphone network, no matter where it's located, according to a report published Thursday. Armed with technical details of a specific provider's current or planned networks, agents secretly attempt to identify or introduce flaws that will make it possible for communications to be covertly tapped, according to an article published by The Intercept. Security experts warned that programs that introduce security flaws or suppress fixes for existing vulnerabilities could cause widespread harm, since the bugs can also be exploited by criminal hackers or governments of nations around the world. "Even if you love the NSA and you say you have nothing to hide, you should be against a policy that introduces security vulnerabilities," Karsten Nohl, a cryptographer and smartphone security expert, told The Intercept. "Because once NSA introduces a weakness, a vulnerability, it's not only the NSA that can exploit it." It's not the first time the US agency has been reported to introduce backdoors into widely used technologies. Last year documents provided by former NSA subcontractor Edward Snowden—the same source for documents supporting Thursday's story by The Intercept—showed that the NSA worked with standards bodies to adopt encryption technologies with known vulnerabilities in them. Two weeks later, the RSA division of EMC warned customers to stop using the default configuration of its BSAFE BSAFE toolkit and Data Protection Manager because it contained code reported to contain an NSA-engineered vulnerability. The program reported Thursday, codenamed AURORAGOLD, has monitored messages sent and received by more than 1,200 email accounts associated with large cellphone operators around the world. One surveillance target is the GSM Association (GSMA), a UK-based group that works with Microsoft, Facebook, AT&T, Cisco Systems, and many other companies to ensure their hardware and software related to cellular technology is compatible. At the same time the NSA has been monitoring the group, other arms of the US government has funded GSMA programs designed to boost privacy on mobile networks. According to The Intercept: The NSA focuses on intercepting obscure but important technical documents circulated among the GSMA’s members known as “IR.21s.” NSA documents show that AURORAGOLD focuses on collecting details about virtually all technical standards used by cellphone operators.
by Dan Goodin http://arstechnica.com/tech-policy/2014/12/exposed-nsa-program-for-hacking-any-cellphone-network-no-matter-where-it-is/ Comments are closed.
|
Archives
March 2021
|
 RSS Feed
RSS Feed